How Do Startups Protect Customer Data?
In today’s digital world, data has become one of the most valuable assets for any business. As more and more transactions move online, companies collect, store, and process vast amounts of sensitive customer information daily. However, with great opportunity comes great responsibility. Startups must implement robust security measures to protect customer data, as any breach could severely damage their reputation and business. This article will explore the various strategies startups can employ to safeguard their customers’ sensitive data.
Implementing strong access controls
One of the most fundamental aspects of data security is access control – determining who within and outside the company has permission to access systems and data and what exactly they are allowed to do. Startups need to establish robust access control policies and technical measures immediately.
Create user accounts for each employee
The first step is to create a unique user account for every employee, contractor, or third party that requires access to company systems or data. Avoid using shared accounts, which make accountability impossible.
Enforce strong passwords
Require solid and unique passwords at least 12 characters long and contain uppercase and lowercase letters, numbers, and symbols. Do not allow commonly used words, dictionary words, or personal information.
Enable multi-factor authentication
For extra security on admin accounts and access to sensitive systems/data, enable multi-factor authentication (MFA), which requires a second verification step in addition to passwords, such as a one-time code sent to a mobile device. This adds an extra layer of protection in case of compromised credentials.
Conduct access reviews
Put in place regular reviews of who has what access rights. Ensure permissions are at most what is required to perform job functions. Timely removal of unneeded access can prevent insider threats.
Limit administrative privileges
Most regular users should not have elevated system-level privileges that grant broad control. These should only be given to specific IT staff when required and revoked immediately after use.
Implement a password policy
Enforce robust password construction and change frequency. Minimum standards should be set for all user accounts. Consider using a password manager for secure storage of credentials.
Use authorization and separation of duties
Clearly define who can perform sensitive actions like financial transactions, data exports, etc. Each individual should have complete control over critical processes.
Properly configure security tools.
Access control systems are only as robust as their configuration. Startups must take time to learn and apply vendor best practices for tools such as Active Directory, LDAP servers, etc.
Monitoring and logging access
It is critical to monitor login activity and implement alerting for any anomalies continuously. Comprehensive logs must also be maintained to enable forensic investigations of security incidents.
These robust access controls form the foundation of data security. When properly implemented using policy and technology, they can prevent breaches stemming from compromised or misused credentials.
Encrypting sensitive data
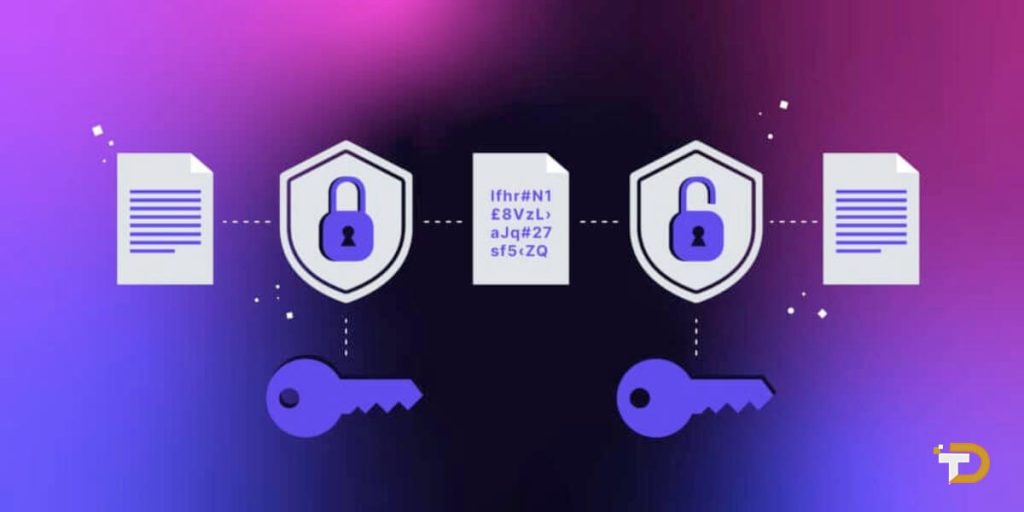
While access controls manage who can reach data, encryption techniques protect the confidentiality of the data itself. Startups must evaluate what information requires encryption at rest and in transit, then implement appropriate solutions.
Encrypting data at rest
All sensitive customer records, financial/banking details, and other classified internal documents stored on company servers or employee devices must be encrypted. This prevents access even if storage media is lost or stolen.
Encrypting data in transit
Any sensitive data transmitted externally over public networks like the Internet needs to be encrypted. This includes customer information sent via email/files and third-party data accessed remotely. Encryption protocols like TLS/SSL should be used.
Encrypt backups
Offsite backups that contain valuable company data and customer records must also be encrypted for protection. This ensures that even if backup drives/tapes are lost or stolen, the data is unusable without the encryption keys.
Use robust, validated algorithms
Only robust encryption standards approved by security experts should be relied on. Startups must avoid weak or obsolete algorithms that can be broken. Keys of sufficient length are also important.
Control and protect encryption keys
Encryption is only as secure as the management of its keys. Startups need processes to ensure keys are correctly generated, stored, escrowed, rotated, and destroyed according to best practices. Access to keys must also be strictly controlled.
Application-level encryption
For maximum protection, even data processed and stored temporarily by applications should be encrypted. This includes sensitive fields users enter, and any logs, caches, reports, etc., created internally.
With the right encryption strategy, startups can rest assured that even if an unauthorized party manages to access storage media or intercept network traffic, they cannot decipher confidential customer information. This significantly reduces data breach risks and impacts.
Securing systems and networks
The systems and infrastructure storing or processing sensitive data must also have robust security controls. Here are some measures startups can take:
Hardening operating systems – Remove unnecessary software and accounts. Turn on automatic updates. Limit login attempts. Enable firewall and restrict ports/protocols. Monitor logs for anomalies.
Patching applications promptly – Apply all security updates from vendors as soon as possible. Outdated apps are vulnerable to known exploits. Consider a centralized patch management system.
Isolating systems by function – Separate databases, web servers, etc. Virtually or physically. Limit lateral movement if one system is compromised. Reduce shared dependencies and configurations.
Implementing firewalls – Use application-aware next-gen firewalls to filter traffic into/out of the network. Detect and block malware, DDoS attacks, etc., before they reach internal systems.
Monitoring network traffic – Deploy intrusion detection and prevention tools. Monitor traffic for policy violations and anomalies indicating cyberattacks or data exfiltration attempts.
Conducting vulnerability assessments – Regularly scan internal and external-facing systems using automated tools. Prioritize and fix high-severity flaws that leave the door open for hackers. Consider penetration testing.
Secure configuration practices – Harden operating systems, databases, and frameworks using the following vendor fast setup guides—Disable unneeded services, ports, accounts, and clear text protocols to minimize the attack surface.
Implementing malware protection – Deploy endpoint detection solutions to identify, quarantine, and remove advanced malware before infecting systems. Ensure all devices used for work have updated antivirus software.
Restricting administrative access – Elevated system access should require multi-factor authentication and be limited only to authorized support staff. Monitor privileged sessions and revoke access immediately after use.
Backing up and testing recovery – Regularly backup critical systems and data. Practice disaster recovery plans to ensure business continuity even if infrastructure fails. Test that backups can be restored successfully and promptly.
With a defense-in-depth approach covering networks, systems, and applications, startups can significantly strengthen their security posture and prevent many external intrusion attempts from succeeding. Timely patching and updates are also essential to plug vulnerabilities exploited by cybercriminals.
Implementing secure development practices
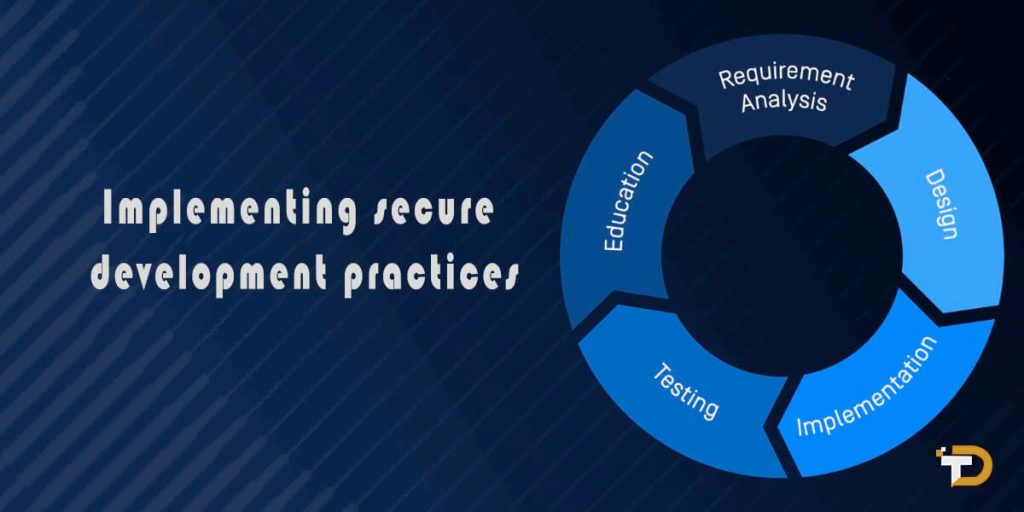
For startups building software products, secure development practices are paramount to prevent flaws that put customer data at risk. Here are some techniques:
Perform threat modeling – Early in development, identify threats, vulnerabilities, and impacts. Prioritize security based on risk levels to focus efforts effectively.
Incorporate security requirements – Include functional and non-functional security needs in requirements documentation and design specifications. Address privacy, integrity, and availability.
Implement secure coding standards – Adopt best practices for secure coding in chosen languages/frameworks and enforce via automated tools and code reviews. Prevent injection flaws, XSS issues, etc.
Conduct security testing – Integrate security testing, such as static analysis, dynamic analysis, fuzzing, etc., into the development cycle to detect and fix vulnerabilities immediately. This includes both automated and manual techniques.
Architect for security – Incorporate security principles like defense-in-depth, least privileged access, and separation of duties into the system architecture. Consider secure open-source components and frameworks.
Address privacy by design – Collect only necessary customer data. Anonymize where possible. Allow users to access, update, and delete their personal information quickly. Obtain explicit consent for sensitive uses.
Configure securely by default – Ensure default configurations restrict access, enable encryption, and require authentication. Remove sample/test accounts and credentials before production deployment.
Train developers – Educate developers on the OWASP Top 10 risks and other prevalent vulnerabilities. Provide secure coding guidelines and code review checklists. Consider specialized security training.
Monitor for vulnerabilities – Use application scanning and runtime protection tools to detect vulnerabilities introduced during maintenance and enhancements. Patch promptly.
Conduct security reviews – Subject designs, code, and architecture to formal security reviews by dedicated security experts at appropriate stages. Identify issues early.
While developing new features and products, startups must remember that security cannot be an afterthought. By instituting secure development best practices, they can help prevent introducing vulnerabilities that compromise user data confidentiality, integrity, or availability.
Read More: Securing Applications with Dynamic Application Security Testing (DAST)
Concluding thoughts
As the threat landscape evolves rapidly, startups must recognize that data protection is a journey without an end. While diligently implementing the strategies discussed provides a strong foundation, ongoing effort, monitoring, and improvement are needed to secure customer information. Some additional considerations include:
- Maintain updated risk assessments and remediate emerging vulnerabilities.
- Procure cyber insurance to transfer risks that cannot be eliminated.
- Consider security standards like ISO 27001 for maturity and third-party validation.
- Build security into vendor management and third-party integrations.
- Designate a CISO/CSO role for dedicated security leadership.
- Conduct regular penetration tests and red team exercises.
- Monitor security news and collaborate with local startup security communities.
By prioritizing data security, startups can give customers confidence while avoiding the potentially devastating impacts of a breach. With a proactive, defense-in-depth approach and continual enhancements, sensitive data remains well protected as businesses grow.





