Securing Applications with Dynamic Application Security Testing (DAST)
With the ever-growing reliance on applications and digital services, ensuring robust security has become a top priority for businesses. As threats evolve rapidly, leaving vulnerabilities unaddressed can put organizations at serious risk. While securing code is crucial during development, continuously monitoring applications post-deployment is equally essential. This is where dynamic application security testing (DAST) plays a pivotal role.
DAST tools simulate real-world attacks to identify vulnerabilities, misconfigurations, and weaknesses that malicious actors could exploit. By making DAST part of your security strategy, you can proactively protect your applications and minimize risks.
What is Dynamic Application Security Testing?
Dynamic application security testing, commonly called DAST, involves analyzing applications as they run without access to source code or internal design details. DAST tools act as “black box” testers, simulating attacks from outside to determine if vulnerabilities exist that could be exploited. Some key things to note about DAST:
- It examines applications in their runtime environment as end-users interact with them. This uncovers issues that static analysis may need to catch up on.
- DAST has no internal insight into code or systems. It security tests applications based on public information like an external hacker would.
- Automated scanners launch attacks involving malicious inputs, observing responses for signs of vulnerabilities like injection flaws or configuration weaknesses.
- DAST is usually non-intrusive, not exploiting any vulnerabilities found but detecting their potential presence.
- Testing is done periodically on applications in pre-production or production environments to catch any new issues introduced over time.
In summary, DAST mimics real-world threats to applications in operation, providing a crucial layer of defense beyond development-time security checks. It helps minimize risks from vulnerabilities that static analysis may overlook.
Why is DAST Important for Application Security?
In today’s digital landscape, applications are central to business operations. They hold sensitive customer data, facilitate essential transactions, and drive service delivery. Any security issues can severely impact user trust, financials, and brand reputation. Some key reasons make DAST vital for holistic security:
- Applications are complex, with multiple components interacting in unpredictable ways. DAST examines the complete runtime environment.
- Code evolves rapidly through iterations. Vulnerabilities can emerge at any time if testing is not continuous.
- Static analysis alone is insufficient as it can’t detect all logic flaws or configuration issues observed during runtime.
- DAST identifies a different set of vulnerabilities than other methods like SAST or manual review.
- It protects applications already in production use from real-world threats before damage occurs.
- Problems missed earlier, which were low risk, could combine over time to become critical vulnerabilities.
- Regular DAST ensures any new vulnerabilities brought in via third-party components or code changes are quickly found.
With applications central to business, DAST has become essential for proactive security that minimizes real risks. Its automated, ongoing monitoring complements development-phase checks for multilayered protection.
How DAST Differs from SAST
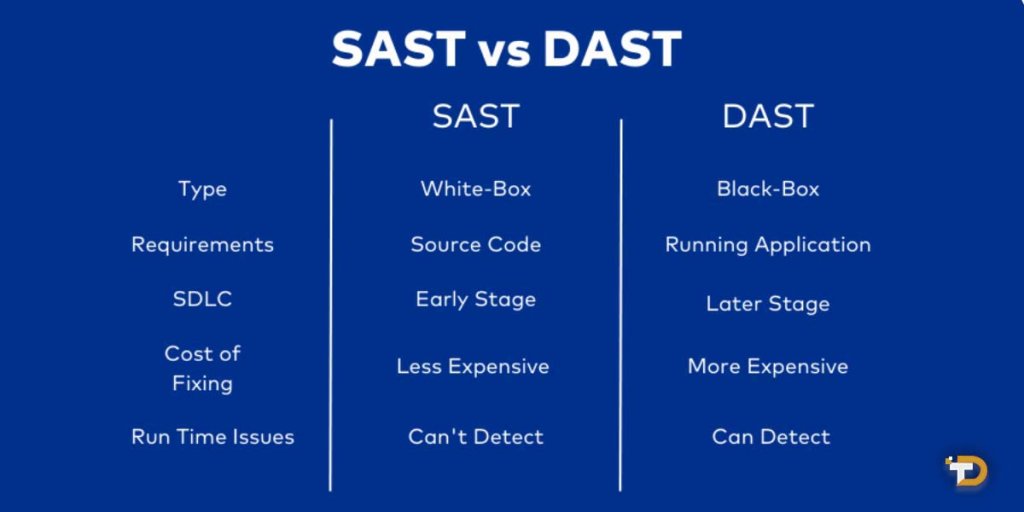
While both DAST and static application security testing (SAST) analyze code for vulnerabilities, they have critical differences in methodology:
- SAST reviews source code structure and syntax without executing it. DAST observes running applications through simulated attacks.
- SAST has internal code visibility but no runtime context. DAST operates as a “black box” tester on complete applications.
- SAST detects flaws like logic issues and insecure code patterns. DAST finds configuration weaknesses and logic bugs only visible at runtime.
- DAST identifies vulnerabilities interactively across the entire application and all components. SAST analyzes individual code modules.
- SAST is best for development, while DAST directly protects currently deployed applications and services.
- Bugs may slip by SAST but be caught by DAST due to its ability to execute all code paths and interactions realistically.
- SAST and DAST provide comprehensive protection, with each method revealing a distinct set of vulnerabilities the other may miss.
Used alongside one another, SAST and DAST deliver multilayered security through complementary static and dynamic analysis approaches tailored for both development and operational environments.
Top DAST Tools for Comprehensive Security
With an understanding of why DAST is essential, let’s explore some top options to consider for your testing needs:
Acunetix
It is known for its robust automation capabilities that can accelerate scans at scale. Acunetix supports scheduling recurring scans to test applications on a set schedule. This makes it well-suited for development and operations teams that require frequent, automated security checks. The automation reduces manual effort and helps integrate testing into the DevOps pipeline. Acunetix also provides robust crawling and spidering features to cover an extensive attack surface. Its reports identify high and medium-risk issues to prioritize for developers.
Burp Suite
As an open-source toolkit, Burp Suite empowers security testers and researchers to conduct highly customized, manual exploration for deeper dynamic testing. It allows interactive manipulation of proxy traffic and provides a browser-like interface to simulate attacks. Burp’s robust feature set has made it a mainstay for penetration testers and an integral part of many security testing engagements. Its extensive attack tools and proxies are often used with automated scanners to supplement results.
Netsparker
Netsparker stands out for its cloud-based SaaS delivery of DAST scans. This simplifies deployment and allows testing to scale on demand quickly. The cloud-hosted scanners also benefit from continuous updates to vulnerability databases. Netsparker leverages machine learning techniques to reduce false positives in results. This helps prioritize legitimate issues for developers. It has also achieved PCI compliance and is frequently relied on by organizations in regulated industries like financial services.
AppSpider by Rapid7
As an integrated part of Rapid7’s InsightVM security solution, AppSpider seamlessly bridges the gap between development and operations. It can automatically detect and test applications through integrations with standard DevOps tools and pipelines like Jenkins, Bamboo, and others. This enables security to be built into SDLC practices from the start. AppSpider also supports hybrid testing across networks to cover both cloud-hosted and on-premise applications simultaneously.
Zed Attack Proxy (ZAP)
As an open-source solution, ZAP removes cost barriers for budget-focused organizations to conduct security testing. It provides the basic functionality of a web vulnerability scanner through an intuitive UI. ZAP effectively crawls and maps applications, then actively tests for common issues. While more limited than commercial offerings, it represents a substantial value for small dev teams or those starting with DAST. The active community also contributes frequent updates. Overall, ZAP offers an accessible first step into the world of DAST.
Checkmarx
Where accuracy is paramount, Checkmarx leverages AI and a team of security experts to meticulously analyze and verify results. This minimizes false positives that can waste developers’ time. By ensuring only confirmed vulnerabilities are reported, Checkmarx helps prioritize remediation. Its seamless IDE plugins also bring security directly to developers within their workflow. Checkmarx excels for applications with stringent security requirements or those subject to compliance mandates.
Qualys
Qualys delivers DAST at a massive scale across hybrid and multi-cloud environments as a multi-tenant SaaS platform. Its continuous scanning capabilities support assessing applications deployed anywhere, from private data centers to all major cloud providers. Qualys automates and streamlines security, compliance, and inventory tasks into a single solution. This holistic view helps reduce security risks enterprise-wide through unified vulnerability management.
PortSwigger
By combining automated scanning with an interactive testing environment, PortSwigger empowers a more hands-on approach. It’s browser proxy and toolset let testers actively craft custom attack simulations. This facilitates deep exploration that scanners alone may miss. PortSwigger proves highly effective when integrated with scanners to supplement results and validate findings. It represents a powerful choice for dedicated penetration testers and researchers.
With so many options, carefully evaluate features to shortlist tools best aligning with your functionality, budget, and integration needs. Proper DAST use delivers ongoing protection as threats evolve constantly.
Read More: The Ethics of Data Collection and Privacy Business Should Know
Conclusion
In today’s digital landscape, applications are the new perimeter. Their security should always be protected from risk, with vulnerabilities going undetected. DAST plays a pivotal role in risk management by continuously monitoring applications as they run, just as real attackers would. It protects deployed services from exploitation by finding issues missed by other checks. Making DAST part of your security strategy delivers proactive protection to protect customer and business data from emerging threats. Regular scans using the right tools for your needs can give you peace of mind.





